Be prepared for audits
Johan West
“You have been selected for a random assisted license verification engagement.”
A variant of a phrase many of our customers have received over the past years. This ‘friendly’ form of announcing a review can be interpreted as harmless, without any significant impact on the business. However, do not fool yourselves as this is just one of many ways software vendors disguise their audit announcements.
Organizations tend to underestimate the business impact of an audit and often see this as part of the ‘organic’ duties of the ITAM team, forgetting the time could have been spent on optimization and other value-adding activities. Just as a reminder, a typical audit in a 1.000 seat company can easily keep 2.000 hours of various stakeholders occupied within your organization from start to closure.
Given the business impact, it is key for your organization to have a process in place to deal with software license audits – and to preferably prevent them to begin with. Simplified the audit process should consist of the following five stages:
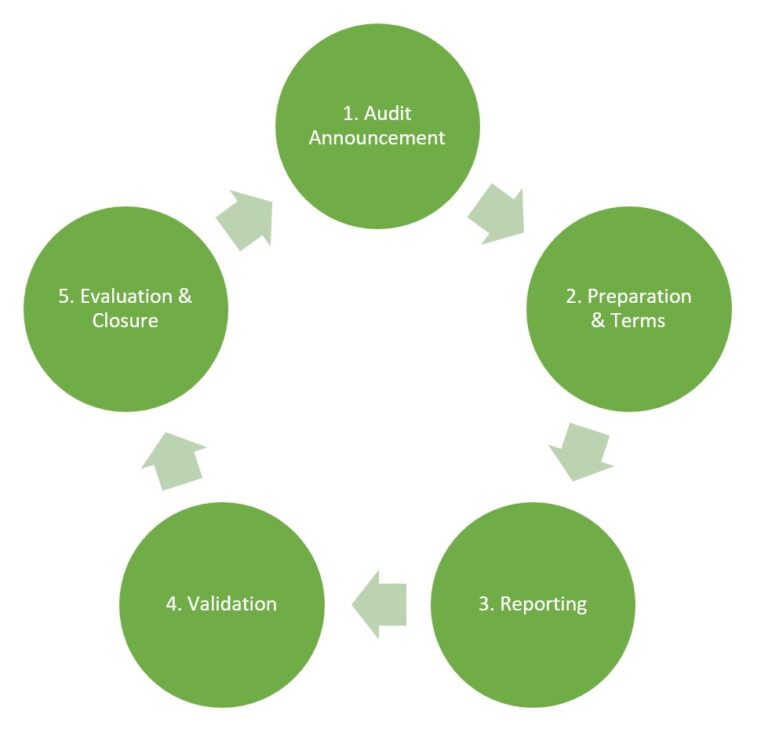
The announcement, in its many forms, can trickle into the organization in various ways. It is key that these announcements find their way to the ITAM team or assigned SME. There should be a protocol in place that prohibits responding to the announcement prior to the due diligence of the ITAM team.
Once the legitimacy of the audit has been established and you are now in talks with the vendor concerning audit guidelines, terms and scope before moving to the reporting stage. Is a self-declaration possible or is the vendor using a 3rd party auditor? Who is extracting the required data and how? On location or remote?
Depending on the agreed-upon data extraction method, your organization might need to run vendor inventory scripts. These scripts might alter some server/device settings so be sure to gather approval from your DB and IT Security office. The gathered data and reported position should be validated by your organization together with the vendor/auditor. How should the data be interpreted? Who can access the various environments? Are there any compliance issues?
In the case of incompliance, your organization could face a number of challenges. On one hand, you could be asked to uninstall your over deployment without further repercussions but on the other, you can receive a significant fine, let alone the backlash from bad publicity. When a vendor is looking for financial compensation for the incompliance it could be beneficial to explore the various options available. You could supplement your license entitlements at a premium, prematurely renew your contract or commit to the latest offering pushed by the vendor. In your settlement and closure with the vendor, it is important to make a couple of agreements think for example of remediation, transition, and/or audit cooldown period.
Lastly, the audit should be evaluated and closed internally. What are the lessons learned? Where did the incompliance originate? Which processes need revision? And of course, how can the ITAM team add value going forward?

